Take Advantage Of Cloud Provider for Boosted Information Protection
In today's digital landscape, the ever-evolving nature of cyber hazards necessitates an aggressive technique towards protecting sensitive data. Leveraging cloud services offers an engaging service for organizations looking for to strengthen their data security steps. By entrusting trustworthy cloud provider with information monitoring, services can use a wealth of safety features and sophisticated modern technologies that reinforce their defenses against harmful actors. The question arises: how can the application of cloud services transform information protection methods and supply a durable shield against possible susceptabilities?
Importance of Cloud Protection
Making certain durable cloud safety and security procedures is paramount in protecting sensitive data in today's digital landscape. As organizations significantly depend on cloud solutions to store and process their data, the need for solid safety and security procedures can not be overemphasized. A violation in cloud security can have serious effects, ranging from monetary losses to reputational damage.
One of the primary reasons why cloud safety and security is essential is the common duty design utilized by many cloud company. While the provider is accountable for safeguarding the infrastructure, customers are responsible for protecting their information within the cloud. This division of responsibilities underscores the value of carrying out robust security procedures at the user degree.
In addition, with the proliferation of cyber dangers targeting cloud settings, such as ransomware and data breaches, companies must stay vigilant and aggressive in mitigating threats. This involves consistently upgrading safety and security protocols, keeping track of for suspicious activities, and educating staff members on ideal practices for cloud protection. By prioritizing cloud protection, companies can much better secure their sensitive information and support the trust fund of their customers and stakeholders.
Data Encryption in the Cloud
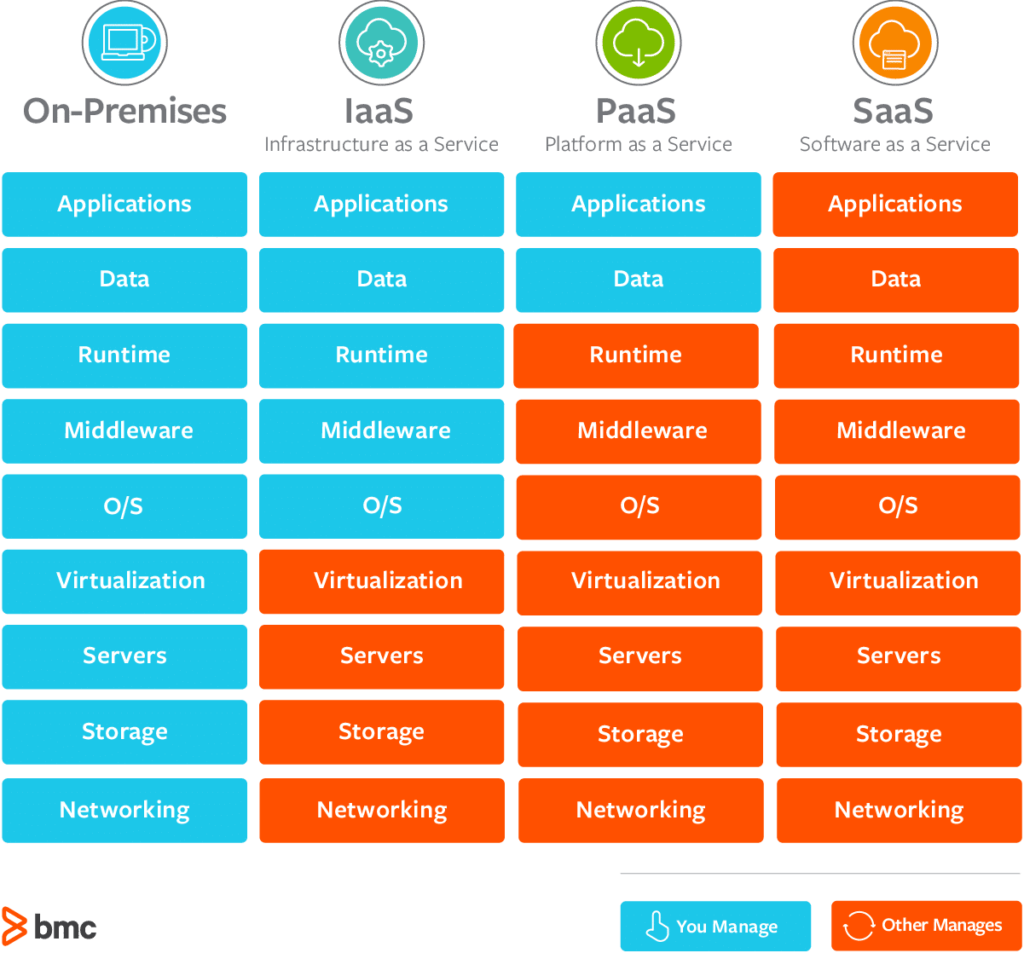
Security in the cloud generally entails using cryptographic formulas to rush data into unreadable styles. This encrypted information can only be analyzed with the matching decryption key, which adds an added layer of safety and security. In addition, lots of cloud solution carriers provide encryption systems to secure information at remainder and en route, improving general data defense. Carrying out robust security practices along with various other protection measures can considerably boost an organization's protection versus cyber threats and protect important details stored in the cloud.
Secure Information Backup Solutions
Data backup remedies play a vital duty in making certain the strength and security of information in the occasion of unanticipated incidents or data loss. Secure data backup options are crucial components of a robust data protection strategy. By on a regular basis backing up data to secure cloud servers, companies can minimize the threats associated with data loss due to cyber-attacks, equipment failings, or human error.
Implementing safe data backup solutions includes picking trusted published here cloud service companies that use file encryption, redundancy, and information stability actions. Additionally, information integrity checks ensure that the backed-up data stays tamper-proof and unchanged.
Organizations should establish computerized backup schedules to make sure that information is constantly and efficiently backed up without manual intervention. Routine testing of information repair processes is also essential to guarantee the effectiveness of the back-up solutions in recouping data when needed. By buying safe and secure information backup services, services can enhance their information safety pose and reduce the effect of potential data breaches or disturbances.
Duty of Access Controls
Executing rigorous gain access to controls is essential for maintaining the security and integrity of delicate details within business systems. Accessibility controls function as a crucial layer of defense versus unapproved gain access to, making certain that only authorized people can check out or control delicate data. By defining who can accessibility specific sources, organizations can limit the risk of information breaches and unauthorized disclosures.

On a regular basis upgrading and examining gain access to controls is necessary to adjust to business changes and evolving safety hazards. Continual tracking and auditing of accessibility logs can aid spot any suspicious tasks and unauthorized gain access to efforts promptly. Overall, robust gain access to controls are fundamental in safeguarding sensitive info and mitigating security dangers within business systems.
Conformity and Rules
Regularly making sure compliance with relevant policies and criteria is crucial for organizations to maintain information protection and privacy steps. In the realm of cloud solutions, where information is often kept and refined externally, adherence to industry-specific laws such as GDPR, HIPAA, or PCI DSS is crucial. linkdaddy cloud services.
Cloud provider play an important duty in helping organizations with conformity initiatives by using solutions and features that align with different regulative requirements. For example, several suppliers use file encryption capacities, gain access to controls, and audit routes to aid organizations satisfy information safety and security requirements. In addition, some cloud solutions go through regular third-party audits and qualifications to show their adherence to sector regulations, supplying added assurance to organizations looking for compliant solutions. By leveraging compliant cloud solutions, companies can boost their data safety and security pose while meeting regulative obligations.
Verdict
Finally, leveraging cloud solutions for boosted data protection is important for companies to safeguard sensitive info from unauthorized accessibility and potential breaches. By carrying out durable cloud safety and security methods, consisting of data file encryption, secure backup remedies, access controls, and compliance with policies, businesses can take advantage of advanced safety and security procedures and know-how offered by cloud company. This aids mitigate dangers effectively and makes sure the privacy, stability, and accessibility of information.

Information backup services play a critical function in guaranteeing the resilience and protection of data in the occasion of unanticipated occurrences or information loss. By regularly backing up data to protect cloud web servers, organizations can minimize the threats connected with information loss due to cyber-attacks, equipment failings, or human error.
Executing secure data backup options includes selecting dependable cloud solution companies that offer encryption, redundancy, and data honesty actions. By spending in secure data backup services, businesses can improve their information security position and minimize the effect of possible information breaches or interruptions.